Hello everyone. Welcome back to yet another blog. It's already Day 22. Only a few more days are left. We are going to save Christmas. Without any further delay, let's move to today's task.
Threats are failing all around me
This task is mainly focusing on Attack vectors and attack surface. An attack vector is any tool, technique or method with which we can attack any system. For example, DOS attacks, phishing, Brute force etc. The attack surface is the surface area of the victim of an attack that can be impacted by an attack vector and cause damage. Taking forward our example of the physical world, the attack surface will include the unarmoured body of a soldier, which an attack of a sword, an arrow, or a hammer, etc., can damage. In cybersecurity, the attack surface will generally contain the following:
An email server that is used for sending and receiving emails.
An internet-facing web server that serves a website to visitors.
End-user machines that people use to connect to the network.
Humans can be manipulated and tricked into giving control of the network to an attacker through social engineering.
We can reduce the attack surface by doing some precautions. For example on the battlefield, Soldiers can use shields to reduce attack surface. In cybersecurity also, You can reduce the attack surface by closing unnecessary ports or using strong passwords. Let's move to today's task now.
Question1
Click on view site.
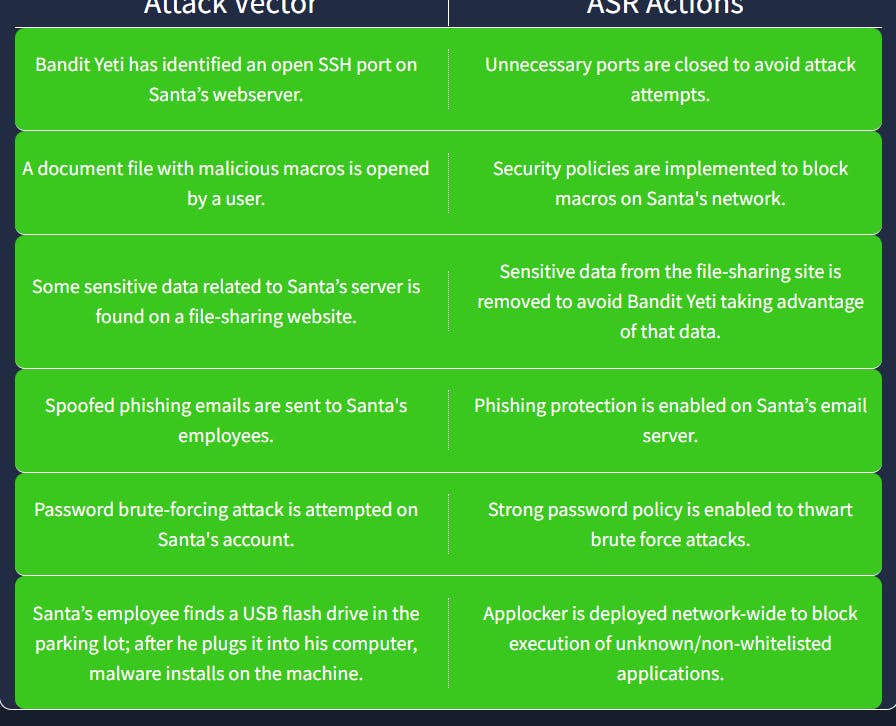
We need to choose the correct attack surface reduction for the given attacks.
In the first attack, we can close unnecessary ports to prevent this attack. Drag and drop the answer.
In the second attack, we can block macros to prevent this attack.
In the third attack, we can remove sensitive information from the file.
In the fourth attack, we can enable phishing protection.
In the fifth attack, we can use a strong password to avoid brute force.
In the last attack, we can deploy Applocker to block some applications.
Click on Next.

We got the flag.

Question2
They are recommnding you Threat and Vulnerability Management module.
Congratulations !! we completed this task. New task will be added tomorrow. Till then you can follow me here for upcoming blogs on the advent of cyber 2022. In the end, you will get a certificate from tryhackme for completing this challenge.
Keep learning and keep spreading Knowledge.
