Hello everybody! Welcome to yet another blog. I hope you are enjoying the advent of cyber. All the tasks are amazing this year. I hope you are learning something new every day. It's time to move to the new task of day 20. Let's do this.
Binwalkin’ around the Christmas tree
This task is focusing on firmware. Firmware is software that provides basic machine instructions that allow the hardware to function and communicate with other software running on a device. The firmware provides low-level control for a device's hardware. In this task, we are going to do reverse engineering. It's like we are going to analyse the firmware to figure out how it was built and what it does. Let's move to the practical part of this task. Open your attack box first.
Question1
So we have three directories. let's move to bin directory first. Notice we have a file called firmwarev2.2-encrypted.gpg. Let's try to perform some reverse engineering here. Use command :
binwalk -E -N firmwarev2.2-encrypted.gpg

The rising entropy edge means that the file is probably encrypted and has increased randomness.
Let's use an older version of firmware and find the encryption keys from there and use those keys in the above firmware. It is located inside bin-unsigned. Change your directory to bin-unsigned. You can see the file firmwarev1.0-unsigned. Use command extract-firmware.sh firmwarev1.0-unsigned

All the outputs are saved in '/home/test/bin-unsigned/fmk/*'
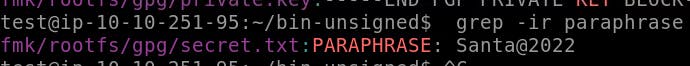
Now we need to find the paraphrase. Use the command grep -ir paraphrase .
Your paraphrase will be visible to you.
Remember this. If you check your fmk/rootfs/gpg/ directory, you can see your public and private key which you got from reverse engineering of older version of firmware. Let's use these keys in our encrypted version. First of all you need to import these keys. Use command :
gpg --import fmk/rootfs/gpg/private.key

They will ask for a paraphrase. Enter the paraphrase that we got above. Santa@2022. In the same way, import public key also.
gpg --import fmk/rootfs/gpg/public.key
Let's decrypt our encrypted firmware. Again go to bin directory and enter command:
gpg firmwarev2.2-encrypted.gpg
Use ls command.
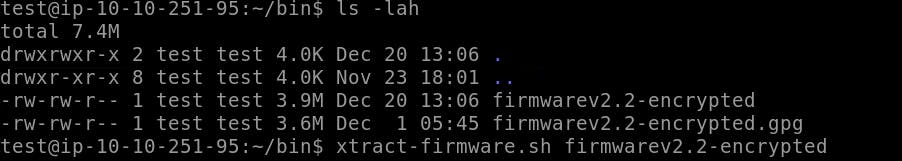
This is our decrypted file. Now we are going to perform reverse engineering. Use command:
extract-firmware.sh firmwarev2.2-encrypted

Our results are saved in /home/test/bin/fmk/. Let's move to this directory.
Go to rootfs directory. You can see a file called flag.txt. Check its content and you got your flag.


Question2
We already found the answer. It is Santa@2022
Question3
For this, use command
ls -ahl *

Scroll down, and you will get your answer in the red line.


Question4
They are recommending you join their discord server.
Congratulations !! we completed this task. New task will be added tomorrow. Till then you can follow me here for upcoming blogs on the advent of cyber 2022. In the end, you will get a certificate from tryhackme for completing this challenge.
Keep learning and keep spreading Knowledge.
