Welcome back everyone to yet another blog. I hope you all are doing tasks daily. Remember, you will get a certificate at the end of this room. So don't lose your consistency and let's move to today's task.
Lumberjack Lenny Learns New Rules
So this room is mainly focusing on Sigma. Sigma is an open-source generic signature language developed by Florian Roth & Thomas Patzke to describe log events in a structured format. The format involves using a markup language called YAML, a designed syntax that allows for quick sharing of detection methods by security analysts. If you are reading about sigma first time, you will find it a bit confusing. But after doing the tasks, all the things will seem pretty clear to you. But before doing the tasks, let's first understand YAML. YAML is a human-readable data-serialization language. It is commonly used for configuration files and in applications where data is being stored or transmitted.
The common factors to note about YAML files include the following:
YAML is case-sensitive.
Files should have the
.ymlextension.Spaces are used for indentation and not tabs.
Comments are attributed using the
#character.Key-value pairs are denoted using the colon
:character.Array elements are denoted using the dash
-character.
So it's time to move to today's task.
Question1
Open your attackbox and go to Your IP Address
You can see an interface something like this :
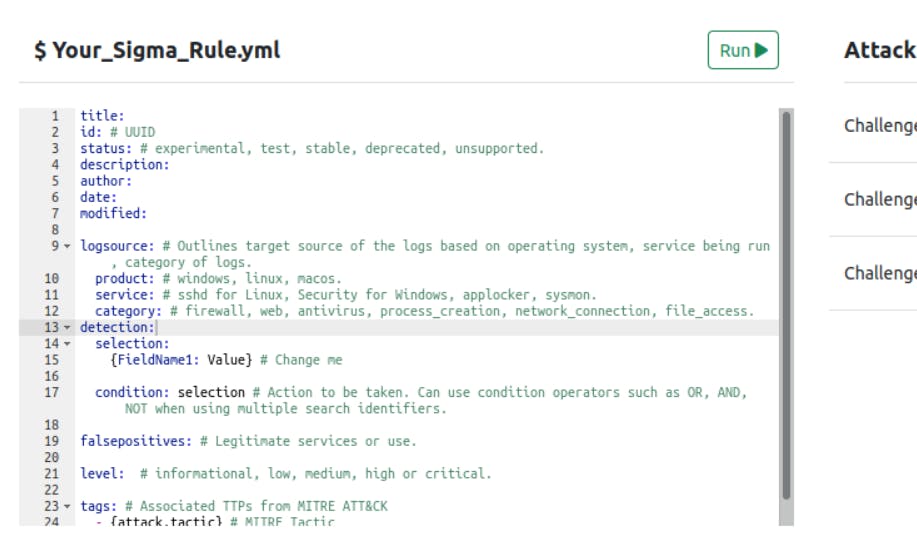
So we have to add some basic rules here:
In title parameter add your title (it could be anything)
Add your id, status, description, author, date and modified according to your will.
Now comes the main part. In the log source, keep it empty. I am using Linux right now, so in the product parameter, I added Linux. TryHackme provided us with some basic rules for account creation in today's task.

Let's use this. In the service parameter, we will use security. Don't change anything in category. Now in the detection parameter, we will specify the rules for how our file will detect whether the account is created or not. So we will put EventID: 4720 as rule. In the level parameter, write low. So our file is ready. It will look something like this.
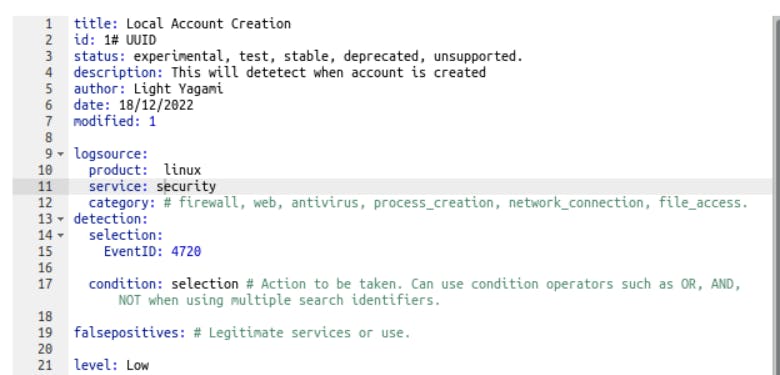
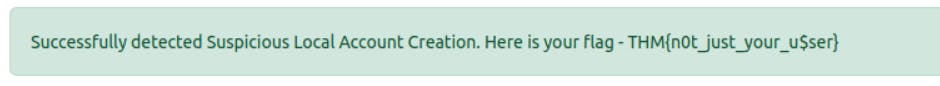
Run the file. You will get your flag.
Question2
When you run the file, you can see a log file is created.

Click on view log. You can see the name of the user.

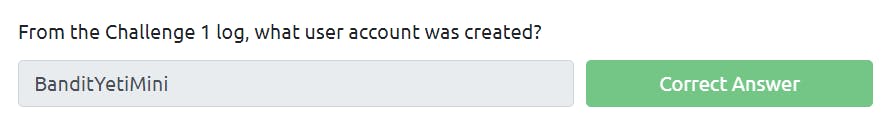
Question2
In challenge 2, we need to discover software. Just like the previous question, add your title, description author etc.
Let's see the rules for Software discovery.

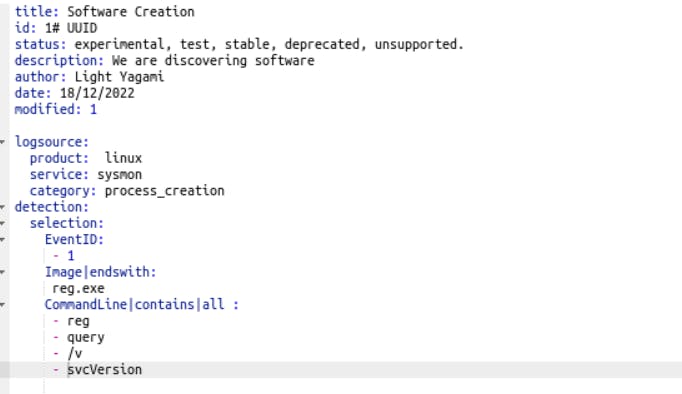
So in this file, we need to change this parameter. Keep the category parameter as process_creation. Service will be sysmon. And the rules are going to be :
EventID :
- 1
Image|endswith :
reg.exe
CommandLine|contains|all:
- reg
-query
- /v
-svcVersion
As you can see, the path of the image is C:\Windows\System32\reg.exe and maybe this path will not be the same in our machine. So we will use Image|endswith and we will give the name of our file. So no need for a path now.
The same goes for the command line path. We will only use those words which will remain the same in all machines so we use CommandLine|contains|all .
And our file will look something like this:
Run your file and see the output.

Question4
Check the log file. You will see your answer.


Question5
First of all, let's see the rule.

Easy, right?
Change category, Service and rules.
EventID :
- 1
Image|endswith :
schtasks.exe
CommandLine|contains|all:
- schtasks
-/create

Run it and grab your flag.


Question6
Check your log file and copy the MD5 hash.


Question7
They are recommending you to complete Yara room.
Congratulations !! we completed this task. New task will be added tomorrow. Till then you can follow me here for upcoming blogs on the advent of cyber 2022. In the end, you will get a certificate from tryhackme for completing this challenge.
Keep learning and keep spreading Knowledge.
