Welcome back to yet another blog. We are on day 16 now. Thanks to tryhackme for releasing such amazing tasks every day. So without any further delay, let's move to today's task.
SQLi’s the king, the carolers sing
So this room is mainly focusing on SQL injection. First of all, let's understand what is SQL. SQL stands for Structured Query Language. SQL lets you access and manipulates databases. There are many basic queries you need to learn in SQL. Now the term comes SQL Injection. In simple terms, we use SQL queries to destroy databases. The database is a very important part of any domain. If somehow, we got access to the database, we can destroy it or manipulate it. For this, SQL injection is used. In this task, we need to use PHP also. This language is used in back-end development. Honestly speaking, I am not quite familiar with PHP language so I won't be able to explain the code. So without any delay, let's move to today's task.
So before moving to questions, visit http://your ip address.p.thmlabs.com/webapp/elf.php?id=2
You can see this type of interface:

See the id parameter. What if we add an ' after 2?

See, you got the table name which is users. This is one way we can check about SQL injection. So why not solve this problem?
Go to http://your ip address.p.thmlabs.com/
Add these credentials.

Question1
Open the file elf.php. Click on Run checks.

We can manipulate the database by injecting some queries. Let's fix this. For this, we need to fix GET['id'] parameter. We can convert whatever the user inputs in the id parameter to an integer. Let's use intval() function. Insert every GET parameter with intval function. Let's change line 4 and line 17.
From this:
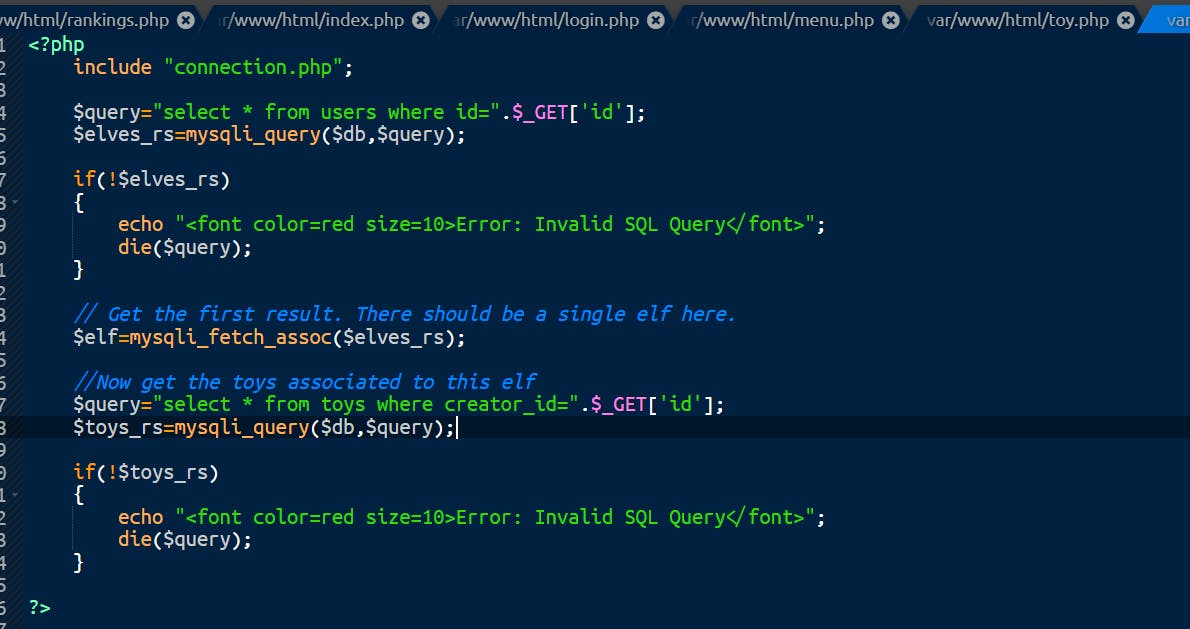
To this:
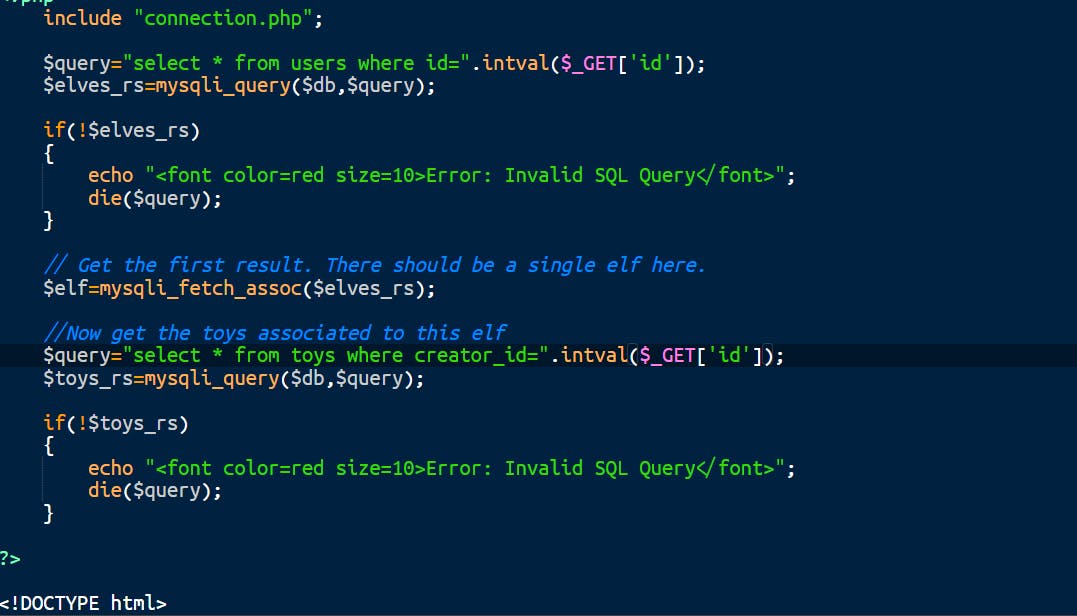
Press CTRL+S. Now click on run checks.

We got our flag.

Question2
Let's move to search-toys.php. Insert this code from line 4
$q = "%".$_GET['q']."%";
$query="select * from toys where name like ? or description like ?";
$stmt = mysqli_prepare($db, $query);
mysqli_stmt_bind_param($stmt, 'ss', $q, $q);
mysqli_stmt_execute($stmt);
$toys_rs=mysqli_stmt_get_result($stmt);
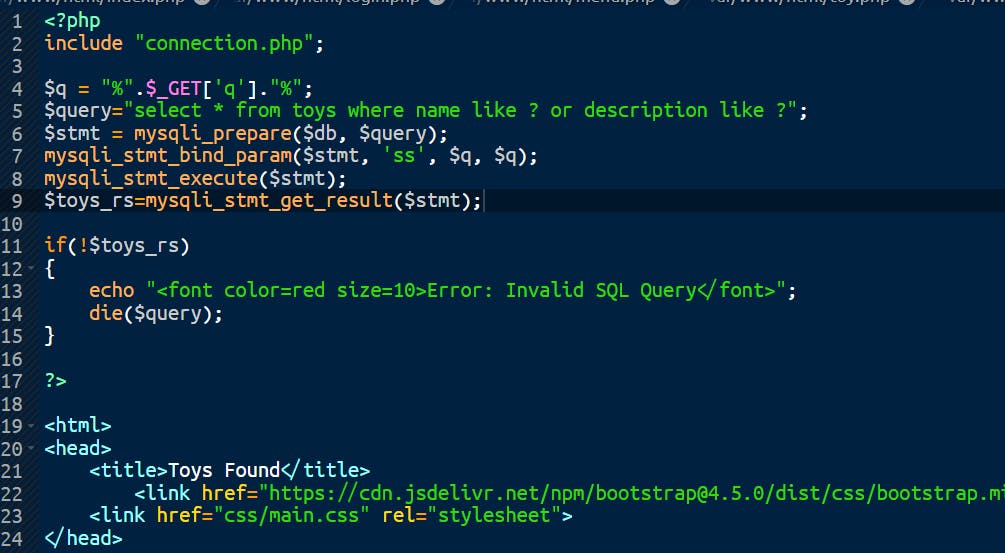

We got our second flag.

Question3
Let's move to toy.php. We just need to follow the same steps which we had done in question 1. Insert every id parameter with intval function. Change Line 4, Line 17 and Line 30. From this :

To this:
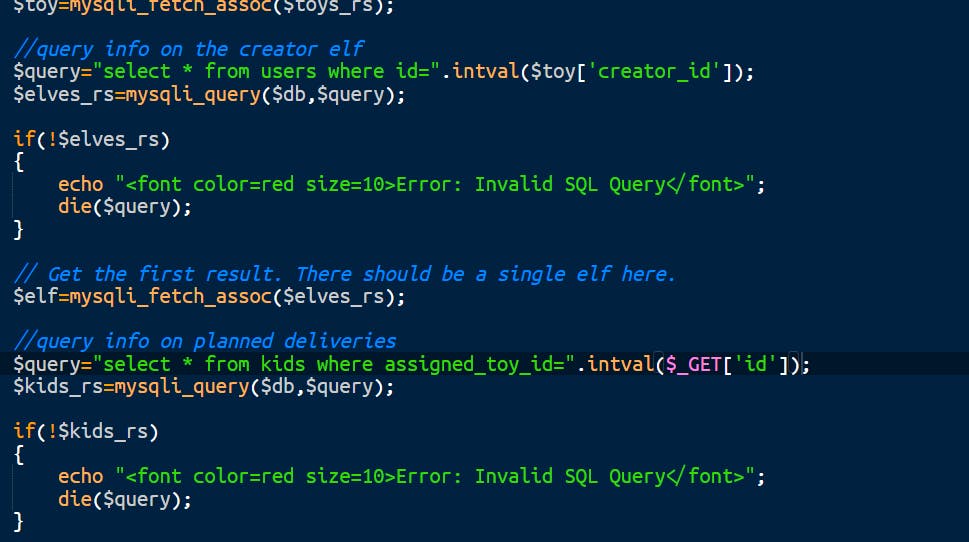

Pretty easy, right?

Question4
Let's move to login.php. Just follow the steps:
In line 8, change the code to this:
$query="select * from users where username=? and password=?";
After line 8, paste this code :
$stmt = mysqli_prepare($db, $query);
mysqli_stmt_bind_param($stmt, 'ss', $username, $password);
mysqli_stmt_execute($stmt);
$users_rs=mysqli_stmt_get_result($stmt);
The code will look something like this :

Run the check and see the answer:

Finally! We got the flag.

Question5
They are recommending you complete this room .
Congratulations !! we completed this task. New task will be added tomorrow. Till then you can follow me here for upcoming blogs on the advent of cyber 2022. In the end, you will get a certificate from tryhackme for completing this challenge.
Keep learning and keep spreading Knowledge.
