Welcome back to yet another blog on Day 14 task. I am trying to cover all 25 days in my blog so follow me so that you won't miss my blog. Without any further delay, let's move to today's task.
I'm dreaming of secure web apps
This room is mainly focusing on IDOR vulnerability. Before IDOR, let me explain to you What is web applications. A web application (or web app) is application software that is accessed using a web browser. To use a web application, we only need a web browser, such as Firefox, MS Edge, Google Chrome, or Safari. But there exist many vulnerabilities in web applications. One of the vulnerability is Poor Access control. Access control is a security element that determines who can access certain information and resources. Suppose, you view a website as a customer but you can perform actions on that website as an admin like changing products or changing the database. It will create a lot of problems for the web application's owner. One of the vulnerability which comes under poor access control is IDOR. It refers to the situation where a user can manipulate the input to bypass authorization due to poor access control. For example, your user_id parameter is 123 and you tried to change the 123 to 124. After changing the parameter, you can see other users' profile information. Although the system should deny them access to the new URL due to lack of authorization, an IDOR vulnerability will let the user display such unauthorized pages. You will get to see the practical of IDOR in this task. So, let's move to the questions.
Question1
Open the attackbox and paste http://<your ip address\>:8080 in your browser

Add your username and password which are given in this task.
Username:
mcskidyPassword:
devtest
You can see this in the url 101.html . Let's try to change this to 102.html .
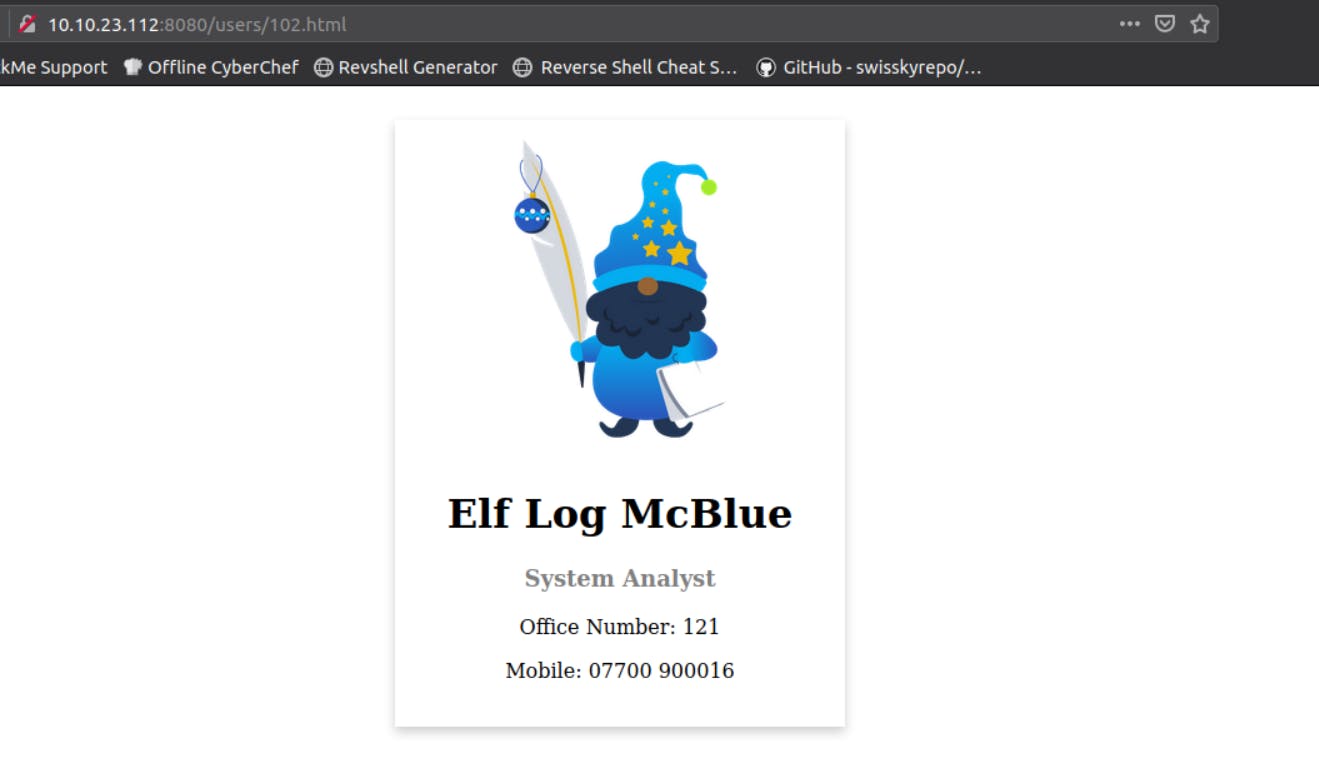
See! We can view other's profiles by changing the parameter. Change this parameter until you found Elf Pivot McRed profile.

I got it in 105.html . You can see the office number in his profile which is 134.

Question2
Now right-click on McRed profile and click on view image.

You can see this in the url 105.png. Let's decrease this number to 104.png. No, it's not there. Decrease the number until you got the flag.

I got it. It was in 100.png.

Question3
They are recommending you to complete room or the Corridor challenge.
Congratulations !! we completed this task. New task will be added tomorrow. Till then you can follow me here for upcoming blogs on the advent of cyber 2022. In the end, you will get a certificate from tryhackme for completing this challenge.
Keep learning and keep spreading Knowledge.
